Getting to the Grey Lock
I run my own mailserver on the net and for some time I have wanted to get email encryption working. My reasons are simply personal education, nothing more. I have no fear that Big Brother is watching me, although I know they are. It’s more for keeping myself up to date on technology.
The two basic types are end-to-end encryption with something like PGP/GnuPG or SMIME to encrypt your messages to everyone you email; and [TLS a.k.a. Transport Layer Encryption] (https://www.feistyduck.com/books/bulletproof-ssl-and-tls/) where the email is encrypted between mail servers on the net, but not necessarily at the endpoints.
Since I don’t have a wide selection of friends using PGP/GnuPG, I’ve settled on getting transport encryption to work reliably. To prove it’s working, I can use Gmail. You can check every message you receive on Gmail to see whether it was encrypted, and if so, what kind of encryption (transport or end-to-end).
Here is an example of a message that was not encrypted. At the drop down on the red lock you can see more detail.
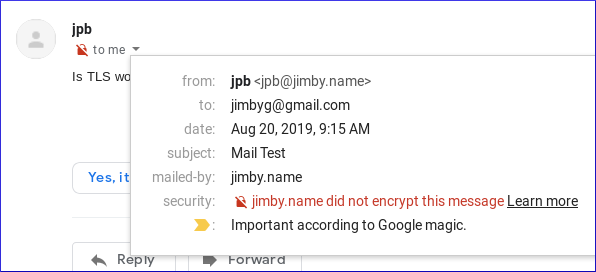
Finding All the Pieces
Encrypting email transport has a number of moving parts. You need mail server software that supports Transport Layer Security (TLS), you need a TLS certificate from a certificate authority (CA), and you need to make adjustments to your Domain Name Server(s) (DNS). In my case I also want to enable Dovecot so I can do IMAP to my mail server from my desktop. That may not be the case for everyone.
Getting Set Up
The easy piece, surprisingly, was getting a free TLS certificate from Let’s Encrypt. Installing and using certbot was easy since there is already a FreeBSD package for it.
For the rest, I’m knowlegable enough to get this all laid out and working, but it is often useful to use a guide someone else has written to give some insight on various technical topics and not waste time on stuff you don’t really need to know to do the task at hand.
One excellent guide that fits my use case is from Rob la Lau over at ohreally.nl. Rob has put together an impressive collection of configuration bits to get
- Postfix mail server
- Dovecot IMAP server with Simple Authentication and Security Layers (SASL)
- Let’s Encrypt certificates
- Sieve mail filtering
- Greylisting spam email
- RBLs - realtime blackhole lists to combat spammers
- ClamAV virus scanning
- Sender Policy Framework (SPF) for DNS
- Domain Keys Identified Mail (DKIM) for DNS
all working together. In my case I only needed Postfix, Dovecot IMAP, Let’s Encrypt, SPF, and DKIM working, so that’s what I focused on. I highly recommend this HOWTO as it is clear, concise, and well written in English. As a bonus, you can read some Dutch while you’re compiling the above bits.
The Results are In
A few hours solid work, and the results are in. I managed to get my IMAP connection to my server and use my Claws email client to send myself an email to my Gmail account.
The email arrived and Gmail shows it was encrypted in transit.
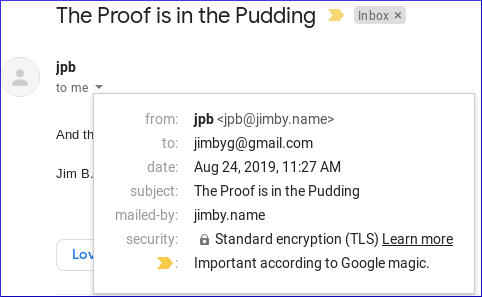
Piece of cake (er, pudding). Thanks Rob!
– Jim B.
